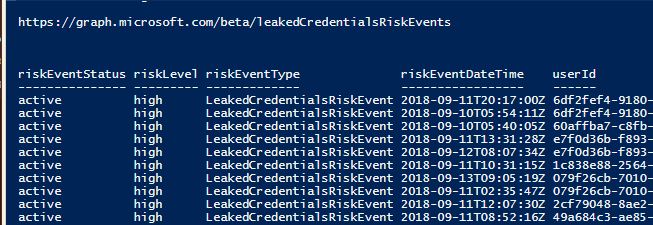
Since we are using SecretServer as our credential store it is of great help to be able to get credentials directly from powershell. This is a small function that connects to secretserver webservices and retrieve a secret based on secred ID. The function will connect to the webservice as the signedin user or by a supplied credential or lastly by a predefined stored credential. To use stored credential I’am using functions from https://github.com/cunninghamp/PowerShell-Stored-Credentials .
Usually you would use the PS credential object directly. To get the password as text you could use it from the PSobject referring to the get networkcredential().
$cred=get-secretid -secretID 2007
$password_As_text=$cred.GetNetworkCredential().Password
Or if you need the password in clear text, displayed on screen, you could specify that as a an argument.
The function is made for my usage, so there is definitive roomfor improvement .
function Get-SecretID
{
param(
[parameter(ValueFromPipeline=$True)]
[int] $secretID,
[pscredential]$sscred,
[switch]$Cleartext
)
$where = 'https://secretserverdnsname/secretserver/winauthwebservices/sswinauthwebservice.asmx'
if($sscred -ne $null){
$ws = New-WebServiceProxy -uri $where -Credential $sscred
}else{
try{
$ws = New-WebServiceProxy -uri $where -UseDefaultCredential -ErrorAction SilentlyContinue
if($ws -eq $null){
if (!(Test-Path Variable:\ssuser)){
throw {
Write-Host "No secretserver user specified or variable 'ssuser' defined.`nThis is to be used by 'get-storedcredential'"
}
}
$credacc=Get-StoredCredential -UserName $ssuser
$ws = New-WebServiceProxy -uri $where -Credential $credacc -ErrorAction SilentlyContinue
if($ws -eq $null){throw{Write-host "Unable to connect to SecretServer"}}
}
}
catch{
}
}
$wsResult = $ws.GetSecret($secretId, $false, $null)
if($wsresult.errors -ne $null){
$Cred=New-Object PSObject
$Cred | add-member -NotePropertyName "Username" -NotePropertyValue $wsresult.errors
$Cred | Add-Member -NotePropertyName "Password" -NotePropertyValue $wsresult.errors
return $Cred
} else {
$u=$wsResult.Secret.Items[1].value.ToString()
$ep = ConvertTo-SecureString $wsResult.Secret.Items[2].value.ToString() -AsPlainText -Force
[pscredential]$Cred = New-Object -TypeName "System.Management.Automation.PSCredential" -ArgumentList $u,$ep
if($Cleartext){
[psobject]$Cred=New-Object PSObject
$Cred | add-member -NotePropertyName "Username" -NotePropertyValue $u
$Cred | Add-Member -NotePropertyName "Password" -NotePropertyValue $wsResult.Secret.Items[2].value.ToString()
$Cred | Add-Member -NotePropertyName "Domain" -NotePropertyValue $wsResult.Secret.Items[0].value.ToString()
}
return $Cred
}
}